Across the globe, governments are putting national security considerations at the centerstage of their regulatory interventions. Similarly, India banned more than 150 China-origin applications due to security concerns.
It is important for India to outline a plausible strategy to address its national security concerns whilst ensuring an open trade environment.
Background
- The rapid pace of digitalisation poses new national security risks for countries like India, a country with over 700 million internet users.
- The multilayered digital ecosystem comprising of infrastructure, devices and applications is complex, and security threats evolve at a breakneck pace.
- This makes it difficult for states to develop an effective response to individual or organisational security threats.
- India therefore has often had to resort to broad trade and market restrictions, rather than nuanced regulation, as the latter requires considerable institutional capacity for oversight and enforcement.
- Now, it is high time that the country adopts a ‘graded approach’ which can help identify a hierarchy of priorities to efficiently employ limited state capacity towards the most critical challenges in digital security.
Analysis
Cyber security as national security
- Cyber security finds its roots in traditional military principles: many of its basic covenants have been adopted from traditional military security principles such as “need-to-know” and “least-privilege”.
- To begin with, the internet as the world knows it today, has evolved from military technology— i.e., the Advanced Research Projects Agency Network (ARPANET).
- Over the years, it has had a transformational impact across the globe.
- In India, this has three interrelated elements:
- the unprecedented adoption of smartphone use in the country
- the presence of a young and technology-savvy population
- affordable access to internet services and devices
- Furthermore, the push for digitalisation by the government, through flagship initiatives under the overarching ‘Digital India’ banner, is also a key driver of the ongoing digital transformation.
|
Digital transactions
- Indeed, the government’s digitalisation efforts have been buoyed by the restrictions on movement that were put in place to respond to the COVID-19 pandemic.
- Consumers are using digital applications to buy consumer durables and necessities, for telemedicine, and for connecting with their friends and family.
- According to the Reserve Bank of India (RBI), India is recording around 100 million digital transactions every day, with a volume of INR 5 trillion ($67 billion).
- This represents approximately a five-fold increase from the 2016 levels.
- The RBI expects digital transactions to continue on a growth trajectory; estimates suggest an increase to 1.5 billion transactions a day worth INR 15 trillion by 2025.
- These figures show that even as the Indian economy has suffered a slowdown because of the pandemic, the country’s digital retail market has earned.
|
- At the same time, cyberattacks have surged.
- India saw a 37-percent increase in cyberattacks in the first quarter (Q1) of 2020, as compared to the fourth quarter (Q4) of the previous year.
- As India’s workforce shift to remote infrastructure, instances of identity theft, and malicious payload delivery has witnessed a spike.
- Breaches by information-stealing malwares like AZORult have been observed in India—they are used to steal users’ browsing history, cookies, IDs and passwords, cryptocurrency, and are also able to download additional malware onto devices.
- The threats to national security can be far more insidious.
|
Types of Cybercrime
- DDoS Attacks: These are used to make an online service unavailable and take the network down by overwhelming the site with traffic from a variety of sources. Large networks of infected devices known as Botnets are created by depositing malware on users’ computers. The hacker then hacks into the system once the network is down.
- Botnets: Botnets are networks from compromised computers that are controlled externally by remote hackers. The remote hackers then send spam or attack other computers through these botnets. Botnets can also be used to act as malware and perform malicious tasks.
- Identity Theft: This cybercrime occurs when a criminal gains access to a user’s personal information to steal funds, access confidential information, or participate in tax or health insurance fraud. They can also open a phone/internet account in your name, use your name to plan a criminal activity and claim government benefits in your name. They may do this by finding out user’s passwords through hacking, retrieving personal information from social media, or sending phishing emails.
- Cyberstalking: This kind of cybercrime involves online harassment where the user is subjected to a plethora of online messages and emails. Typically cyberstalkers use social media, websites and search engines to intimidate a user and instill fear. Usually, the cyberstalker knows their victim and makes the person feel afraid or concerned for their safety.
- PUPs: PUPS or Potentially Unwanted Programs are less threatening than other cybercrimes, but are a type of malware. They uninstall necessary software in your system including search engines and pre-downloaded apps. They can include spyware or adware, so it’s a good idea to install an antivirussoftware to avoid the malicious download.
- Phishing: This type of attack involves hackers sending malicious email attachments or URLs to users to gain access to their accounts or computer. Cybercriminals are becoming more established and many of these emails are not flagged as spam. Users are tricked into emails claiming they need to change their password or update their billing information, giving criminals access.
- Online Scams: These are usually in the form of ads or spam emails that include promises of rewards or offers of unrealistic amounts of money. Online scams include enticing offers that are “too good to be true” and when clicked on can cause malware to interfere and compromise information.
|
Finding a balance between ‘trade’ and ‘national security’
- The imperative is to find a balance between trade priorities and national security. Indeed, digitalisation has made economies vulnerable to security threats.
- This is because of the nature of the internet being a bidirectional medium that offers an enhanced level of access to information about individuals, thereby potentially compromising their privacy and security.
- Social-media platforms, for example, make users susceptible to manipulation.
- There have been cases in different parts of the world of threat actors using social media to influence electoral outcomes and threaten social stability.
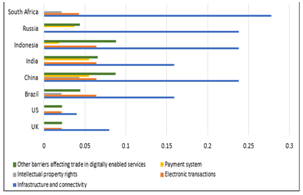
- According to the Organisation for Economic Cooperation and Development (OECD)’s Digital Trade Service Restrictiveness Index, only four countries out of 46 surveyed by the OECD have lowered their trade barriers during the period 2014 to 2019.
- The majority either heightened their digital services trade restrictiveness or maintained the same level.
- In India, restrictiveness index increased from 0.21684 to 0.34339 during the same period.
Evaluvating India’s Approach
- Governments regard strategic industries and critical infrastructure as key to countering internal and external threats to national security.
- “Strategic industries” include those that are crucial for the economic development of a country
- “critical infrastructure” are sectors that are vital not only for the economy, but on other pillars of society as well (e.g. power, transportation, and finance).
- India’s Information Technology (IT) Act defines Critical Information Infrastructure (CII) as computer resources whose incapacitation or destruction will have debilitating effects on India’s security, economy, public health, or safety.
|
National Critical Information Infrastructure Protection Centre (NCIIPC)
- The National Cyber Security Policy (NCSP) 2013 delineates CII protection as a national priority that requires the sharing of responsibility between the public and private sector.
- The policy outlines the importance of establishing a National Critical Information Infrastructure Protection Centre (NCIIPC).
- The Indian government has thus established a nodal NCIIPC under the National Technical Research Organisation (NTRO), the intelligence agency under the Prime Minister’s Office.
- The NCIIPC’s key functions include:
- identifying all elements of CII for government approval
- issuing threat-related advisories
- offering requisite leadership and coordination to effectively respond to threats against identified CIIs.
- It is also assigned the responsibility to coordinate and share strategic information with the CERT-In.
|
- At present, CIIs under each critical sector are identified based on parameters such as “functionality; criticality; scale; degree of complementarities; political, economic, social and strategic values; degree of dependence; and sensitivity.
- There are six critical sectors, according to the government’s definitions: banking, financial services, and insurance; transport; telecommunications; power and energy; government; and strategic and public enterprises.
- Operational technology (OT)—which helps in monitoring, managing, and controlling physical devices and related functions—is a vital cog within the CII sectors.
- These systems are collectively known as cyber physical systems.
- Cyberattacks on cyberphysical systems can therefore risk disruption of services in the critical sectors such as hydropower plants and dams, satellites, power plants, and electricity grids.
- Reliance on OT due to increased digitalisation, has in turn heightened the vulnerabilities of CIIs.
|
Governing structure
- Information Technology Act, 2000: It provides legal recognition to e-commerce and e-governance and facilitates its development as an alternative to paper-based traditional methods.
- Crime and Criminal Tracking Network System (CCTNS): It is a nationwide network infrastructure for evolution of IT-enabled state-of-the-art tracking system around “investigation of crime and detection of criminals”.
- National Cyber Security Policy, 2013: It provides for:
- To build a secure and resilient cyberspace.
- Creating a secure cyber ecosystem, generate trust in IT transactions.
- Creation of a 24 x 7 National Critical Information Infrastructure Protection Center (NCIIPC).
- Indigenous technological solutions.
- Testing of ICT products and certifying them.
- National Technical Research Organization (NTRO): NTRO is a highly specialized technical intelligence gathering agency. It develops technology capabilities in aviation and remote sensing, data gathering and processing, cyber security, cryptology systems, strategic hardware and software development, and strategic monitoring.
- CERT-In: CERT-In has been designated to serve as the national agency to perform the following functions:
- Collection, analysis, and dissemination of information on cyber incidents.
- Forecast and alerts of cybersecurity incidents
- Emergency measures for handling cybersecurity incidents
- Coordination of cyber incident response activities
- Issue guidelines, advisories, vulnerability notes and white papers relating to information security practices, procedures, prevention, response and reporting of cyber incidents
- National Cyber Coordination Centre (NCCC): It is a critical component of India’s cyber security against hackers and espionage as well as to track terrorist activity online.
|
What India can learn from the world?
- ISO 27701: India can consider adopting ISO 27701, which is considered as a privacy extension of the 27001 standard.
- The ISO 27701 standard helps an organisation in establishing a framework for the protection of privacy, provides guidance on how institutions should handle sensitive personal data, and helps in demonstrating compliance with different privacy regulations across the world.
- It also specifies a Privacy Information Management System (PIMS) and provides a framework for managing Personally Identifiable Information (PII).
- Common Criteria Certification Scheme: The use of the Common Criteria Certification Scheme, which has been adopted by jurisdictions such as the US, Singapore, and the European Union, also offers a useful alternative.
- A critical advantage of mandating Common Criteria Certification to a specific entity is the relative ease in rolling out such obligations. India is already a member of the Common Criteria Mutual Recognition Arrangement (CCMRA).
- This arrangement enables the recognition of evaluation done by one member country in another.
- More than 30 countries have signed the arrangement so far, including the US, Singapore, Japan, Canada, and Australia.
|
Domestic regulators such as the Securities and Exchange Board of India (SEBI) have also embraced the Common Criteria Scheme.
|
Certification Body in India
- Standardisation is a crucial component in developing cyber-resilience.
- In India, the Standardisation Testing and Quality Certification (STQC) Directorate, which is attached to the Ministry of Electronics and Information Technology (MeitY) acts as the Certification Body.
- The Directorate has established testing centers in West Bengal, Maharashtra, Karnataka, and Delhi.
Suggestive measures
The Indian government should consider adopting a risk-based and graded approach to counter national security risks posed by digitalisation.
- Number of Indian users: The simplest way of operationalising this would be to define a user-based threshold that indicates a sustained and significant involvement of a platform. Needless to say, the threshold should be a proportional representation of India’s total population. The threshold is premised on the principle that sustained engagement and active participation of users can make the business vulnerable to external threats, and therefore the need to adopt a more robust security architecture.
- Type of Data collected/processed.The second criteria is the type of data collected or processed by a business entity. The categorisation is based on the overall assessment of the following parameters: nature of data processed i.e. sensitive data or not; type of processing activity i.e. collection, use, or disclosure; risk of harm resulting from any processing undertaken; and whether an entity is using any new kind of technology to carry out the processing activity. This criterion is premised on the fact that collection of sensitive data—such as biometrics and genetic information—allows the business to undertake large-scale profiling and can significantly endanger security interest in case of a breach.
- The sector in which the entity operates.To identify if the activities have a likely impact on the strategic or critical interest of India.
Closure
The number of internet users in India is expected to reach one billion by 2025. As consumers shift increasingly to digital alternatives, businesses are also innovating constantly to serve changing needs. However, as data-driven businesses occupy centerstage in the global economy, the concomitant cyber-threats raise security concerns for governments across the globe.
In this regard, India will have to carefully curate a strategy to ensure that the country can exploit the economic potential of the digitalisation of the economy, while developing cyber-resilience. Besides developing a robust technical infrastructure to minimise cyber-risks, other measures such as the enactment of a data protection law, and encouraging businesses to train and educate the workforce should be pursued. These measures can help in tackling the ever-evolving cyber threats and risks, and lay the foundation for a safe and secure future.
